Phishing Emails | The Complete Overview
Business is no longer the same as it was. The internet has transformed the world from a collection of pagers to completely distributed companies and entirely new items of value, such as crypto-currency.
As the world has shifted online, the criminal world has followed, and even led in some cases. Cyber crime has spiralled and is impacting every business across the world.
Unfortunately, with technology on the rise, there's more room for cyber crime in 2018. According to the Cyber Security Breaches Survey 2018, 43% of businesses were a victim of a cyber security breach in the last 12 months. In the U.S., the state of California lost more than $214 million through cyber crime alone.
Before you can stop it, you need to understand it.
Phishing is a low-risk crime that can deliver huge payoffs, and today cybercrime is relentless, impacting hundreds of millions of people every year. The costs are steep, from compromised intellectual property, personal, and business information, to damaged reputations and lost opportunities, and with the rise of cryptocurrencies, and untraceable payments as a result, phishing can only be expected to rise.
Common forms of cybercrime
The most common forms of cybercrime include:Nowadays, all digital devices (including computers, tablets, and smartphones) are connected to the internet.
The most common form is phishing.
Phishing is a form of fraud in which an attacker masquerades as a reputable entity or person in email or other communication channels. The attacker uses phishing emails to distribute malicious links or attachments that can perform a variety of functions, including the extraction of login credentials or account information from victims. From http://dilbert.com/strip/2005-08-12
From http://dilbert.com/strip/2005-08-12
Businesses and their employees are a primary focus for phishing scammers. This is often because the types of scams that can be inserted into a business email server can result in more emotional manipulation.
30% of phishing emails in the U.S. are opened That's almost one-third of all emails, according to Verizon's 2018 Data Breach Investigations Report.
And indeed, what's happening with phishing attacks against both consumers and businesses is a what's known as social engineering. Phishing attempts work toward 4 appeals: fear, greed, obedience, and helpfulness. Especially as it applies to business employees, it's easy to imagine how an employee might be manipulated into clicking on a phishing attack utilizing any of these appeals.
For example, a phishing email scam warning an employee about an open enrollment deadline for healthcare could lure in enough clicks do to reasonable damage. Employees may feel both the fear of missing the deadline and the need to obey the command to sign up before the deadline has passed, potentially clicking on the link and entering personal information or downloading malware before realizing the mistake.
Scam artists continue to hone their skills of behavioral manipulation, persuading unwary consumers and business employees to click on phishing emails, links, and web pages: As of 2015, 97 percent of consumers could not correctly identify phishing scam emails. The McAfee survey had 19,000 respondents from around the world, highlight the global impact of phishing scam emails in general. (Source: McAfee) Unexpectedly, those 55 or older are more likely to know what phishing is over their younger peers aged 18-29. 71 percent of those 55 or older effectively identified what phishing is, as opposed to 61 percent for the other age group. (Source: Wombat Security) Germans and UK residents were also more likely to successfully define phishing versus their US counterparts. Over 70 percent of Germans and UK residents could define phishing correctly, versus just 61 percent of US respondents. (Source: Wombat Security)
How phishing got its name
The history of the term phishing is not entirely clear.One common explanation for the term is that phishing is a homophone of fishing, and is so named because phishing scams use lures to catch unsuspecting victims, or fish.
Another explanation for the origin of phishing comes from a string -- <>< -- which is often found in AOL chat logs because those characters were a common HTML tag found in chat transcripts. Because it occurred so frequently in those logs, AOL admins could not productively search for it as a marker of potentially improper activity. Black hat hackers, the story goes, would replace any reference to illegal activity -- including credit card or account credentials theft -- with the string, which eventually gave the activity its name because the characters appear to be a simple rendering of a fish.
Types of phishing
As companies continue to educate their employees in cyber-defense and deploy anti-phishing strategies, cybercriminals continue to improve their existing phishing attacks and roll out new types of phishing attacks.
Some of the more common types of phishing attacks:
This article will provide details on Spear Phishing
Spear phishing attacks attacks feature highly sophisticated targeting, usually using information specific to the victim that has been gathered to more successfully represent the message as being authentic. along with a mix of potential tactics (including social engineering, email spoofing, or computer intrusion) to fool the target into believing that an email is coming from an executive within the organization or from a trusted partner. The key strength of spearphishing attackes are that they don't look spammy. They are well crafted, built and link properly, so as not to cause suspicion.Spear phishing emails might include references to coworkers or executives at the victim's organization, as well as the use of the victim's name, location or other personal information. Sometimes they are even email chains that are replied to.
They are the weapon of choice of cyber criminals currently, because they WORK.
Often, the primary purpose of spear phishing attacks is to manipulate the target into executing an unauthorized transfer of funds. According to the FBI's 2017 Internet Crime Report, in 2017 the Internet Crime Complaint Center (IC3) received 15,690 complaints with adjusted losses of more than $675 million.
This figure is nearly twice the 2016 figure of $360 million.
Firebird Analytical Solutions & Technologies estimates that the average successful spear phishing attack is worth $130,000 to the cyber criminal. The question is can your business afford $130 K for clicking an email?
These are some current statistics from https://resources.infosecinstitute.com/the-trends-in-spear-phishing-attacks/
Compared to a general Phishing campaign, Spear Phishing campaigns cost 20X per victim, and the return is 40X greater. A Cyber attacker will spend an enormous amount of time also trying to find a hidden "crack" or "hole" in the organization in as a stepping stone to collect the relevant information/data on their victim
Most spear-phishing attacks are basically bank heists. They want to steal your cash. As a result they will often impersonate your financial institutions, getting you to log into a fake website, steal your credentials and then spend your money.
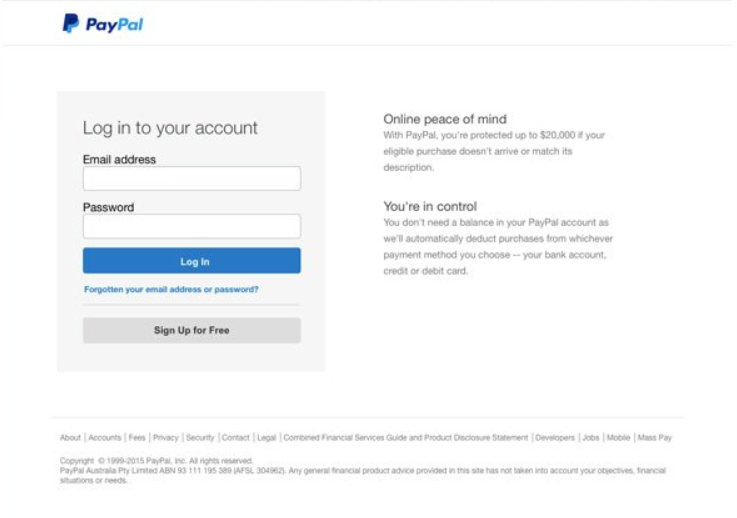 An example of a spear-phishing paypal login in form
An example of a spear-phishing paypal login in form
It's happening every day. Here are some latest incidents, source [https://resources.infosecinstitute.com/the-trends-in-spear-phishing-attacks/#gref]



